There is a load of noise being generated right now about Wikipedia being filtered by six of Britain’s largest ISPs because of instances of child pornography being found on certain articles. In a rather opportune coincidence, I came across the effect of this filtering mechanism a little over a week ago because of problems accessing some Ning networks that I am members of/operate with – importantly none of these are child pornography sites but are engineering and software coding related ones including the Ning Developer and Network Creator networks. I am not an apologist for those despicable scum, just someone who managed to get a written explanation of the transparent caching mechanism that is used by one of these ISPs – Plusnet. I thought it would be useful to post the description in full for those like Cory Doctorow, so they could understand the mechanism better rather than have to reverse engineer it.
My problems stated when I received posting timeouts on trying to sign up to the Ning Developer network, which produced the interesting error message of:
(104) Connection reset by peer
An error condition occurred while reading data from the network. Please retry your request.
Generated Tue, 25 Nov 2008 11:08:54 GMT by pcl-iwfcache02.plus.net (squid)
and in the end this message was being generated by problems in the Ning network configurations, which they resolved but it acted as the canary for revealing the transparent caching solution which was operating. Why it was operating was not particularly clear. After the error went away with Ning, I thought nothing more until a Tweet response came back from someone else on Plusnet who operated Nings, to which I replied with a comment about Plusnet and transparent caching. Now Plusnet, like other ISPs, are now on Twitter and there was an immediate response and a reference to a new update on my open ticket to Plusnet about my problems. The response was:
Dear Mr Nock,
Apologies for the confusion but all of your traffic does not pass through these proxies. Their purpose is to prevent access to websites that are listed on the Internet Watch Foundations child abuse lists – http://www.iwf.org.uk/
Our routers firirstly check the IP address of the server that’s hosting the URL you’re trying to access. If they determine that the IP address is also used to host one of the websites on the IWF list then your request is passed to the IWF proxies.
A lookup is then done and if the address you’re trying to access matches one on the list then the request is denied. If it doesn’t match, then the request should be honoured and you shouldn’t experience any problems.
Here’s a visual depiction – http://community.plus.net/wp-content/uploads/2008/12/iwf_process_flow.png
This isn’t foolproof though and we have seen issues akin to what you’re experiencing with other shared sights like Yahoo profiles and Flickr. The URL you’re trying to access will be perfectly safe (and won’t be on the IWF list) but the process is breaking down somewhere.
I’ll do some playing around with ning on a test line and assuming I can replicate the problem I’ll raise it internally so we can fix it for you.
Kind regards,
*** ******
For those interested, here is the visual depiction referenced above:
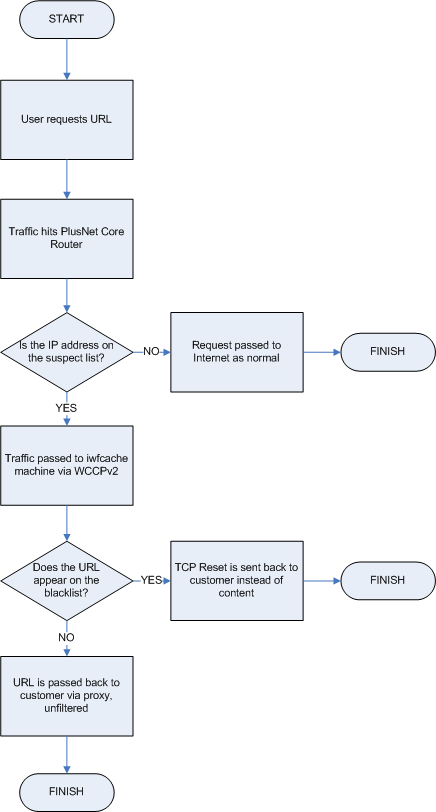
I was initially concerned that all my content was passing via this transparent cache – a privacy and performance concern – but as described above this does not happen unless I hit the criteria set by the ‘suspect list’. However it seems that the suspect list is a little suspect, particularly for shared sites like Ning, Flickr, and now as we see Wikipedia.
[…] Great Firewall of Britain (Thanks, Seth!) […]
Workaround for the affected sites could be using HTTPS. For the cost of some overhead, the ISPs and other wannabe censors will be denied access to the HTTP request content.
[…] The other issue is the existing mechanism is designed very well for web pages and graphic images, but is it suited and scalable to deal with video content over RSS, Torrents and HTTP? have a look and you decide. […]
Would seem anything on BT lines going through a BT owned ISP is to be spyed on. What right has BT and plusnet to send you via a third party proxy which you are not aware of which is off their network. This can compromise your privacy, your human rights it is stil interception of a communication without consent. Which is against RIPA while doing this they are allowing your thirdparty outside the ISP access to your computer the proxy could gather information you didn’t know it was gathering.
[…] About Great Firewall of Britain […]
[…] Great Firewall of Britain […]
@Shaddack – unfortunately that wouldn’t help if the ISPs are filtering by IP address. The web sites would need to get all new IPs from their providers. The easiest solution for users is probably TOR or paying for VPN/Tunnel access to a server in a another country and tunnelling all your web traffic through it.
“Would seem anything on BT lines going through a BT owned ISP is to be spyed on. What right has BT and plusnet to send you via a third party proxy which you are not aware of which is off their network.”
Hi there,
Just for the record, I’d like to let it be known that our IWF proxies are definitely *not* third party. The kit is owned by us and resides on our network in one of our London data centres.
It’s probably also worth noting that we don’t keep logs etc. of the IP addresses that go through the proxies and the only purpose of this filtering is to protect our customers from inadvertently accessing indecent images of children.
We’re currently looking into the WikiPedia situation to see if there’s any way we can restore the ability to edit articles anonymously for our customers. As an interim solution, our customers can still edit pages if they create a WikiPedia account and log into the website first.
Bob Pullen
Plusnet
Thanks Bob, it would be good to hear more information about how multi-hosted services like Ning, Flickr and Wikipedia can be better served in these situations, and also clarify the due diligence around whether content is filtered/blocked for other reasons, such as in the case where parties simply do not like the content rather than it matching legal blocks. Also, does Plusnet have a comment about how the IWF decides the blocking criteria?
[…] #2: Great Firewall of Britain (The Nock […]
Can you check if Plusnet has filters on 68.180.151.74 as well?
One way to test it is to visit
http://www.newdesignconcepts.net/logs/access.log
then refresh again the page. If you see the transparent proxy IP address, then that IP is in the list as well.
@ThinkConstructive, yes the IP of one of our proxies appears in that list.
@Ian, the only content we filter against is what’s contained on the IWF’s child abuse list. The processes they use to decide what goes on this list are explained in more detail here – http://www.iwf.org.uk/public/page.148.htm
I personally think these processes are quite reasonable, however on this occasion I suppose they may have made a poor judgement call.
If you’ve not heard it already, there was quite an interesting interview on the Today programme this morning about the WikiPedia/IWF thing – http://news.bbc.co.uk/today/hi/today/newsid_7770000/7770832.stm
I’m concerned about this service for two reasons: choice and privacy.
Choice: I’d be interested in the community’s view on using OpenDNS to proactively self-protect against access to unsuitable sites. I have chosen that mechanism to provide a level protection against my family unintentionally accessing sites hosting inappropriate content.
In using OpenDNS I am consciously opting into a service whereas these six ISPs are making a privacy decision on their customers behalf, certainly my preference lies with the former.
Choice, I fear, is not something the customer will be afforded on this matter. The level of knowledge required to exercise choice is beyond the vast majority of internet users.
Privacy: while this IWF advised filtering scheme is not intended to provide a means for tracking an individual’s surfing habits, and I have no information to suggest that it is used for any purpose other than discussed, it’s a solution that might easily be used track any individual’s internet traffic.
Rather than enacting law to mandate ISPs, hosting providers, etc, to overtly track and log traffic & site visits, there is a school of thought that forensic investigation should exploit existing sources of information for history tracking.
It appears that this filtering mechanism acts on all the information that would be useful to agencies who may be interested in a user’s specific Internet connections.
Maybe logging isn’t a bad thing, the police already have access to a subset of our telephony call data records by request but I’d still prefer information and choice over how my privacy is compromised. The IWF’s initiative doesn’t seem to provide either.
Don,
OpenDNS does not bypass the filtering. The way the filtering appears to work is that they extract the IP address of the website of the URL. Thus any Web access to that IP address goes through filtering.
The problem is that with virtual hosts, many many irrelevant websites are also targeted.
there are a few unsavoury things on wikipedia that any kid could get on to.
@Bob Pullen – does it matter who owns the actual kit if it’s operated by a “self-regulating” third party like IWF? I’d reckon that seems like a third party proxy to most people.
It’s interesting to note that your IWF proxies block “potentially illegal” material and not just what they claim to be actually illegal. I mean, a bottle of amaretto could be described as “potentially illegal” because I could hit someone with it!
@Bob Pullen – are you able to confirm or deny whether the IWF have administrative access to the IWF proxies owned by your company, or whether they just regularly retrieve a file of (presumably hashed) URLs from the IWF?
@MJ Ray – it depends on what, if anything, Bob is able to say in response to my question above… 🙂
[…] with me in jail! I shoulda stuck with mocking Muhammed in comics!) As Wikipedia (which I think is banned in the UK now, right?) states succinctly: The PROTECT Act of 2003, a comprehensive bill related to many aspects […]
Firstly Wikipedia itself is not banned, only that access to Wikipedia passes through transparent proxies that cause the page that is dodgy to be not available in the UK, with no logging taking place based on Plusnet’s responses and other information gathered from the Internet.
Secondly, the cartoon depiction of sexual acts between minors is as illegal in the UK as it is in Australia. It matters not that they are cartoons or real, as long as the meaning is sexual. I think however a full legal opinion would need to be sought for this, but you can bet that the realism of the depiction does count and Lisa Simpson is real enough but your stick figures are not. However associate those stick images with the words you have so placed on your site then I think you could be going some way towards demonstrating important circumstantial evidence that you are indeed committing a criminal offence. However, I am not a lawyer as I said and a full legal opinion would need to be obtained… This in itself is pertinent to the discussions today as the IWF are not a full legal body (for opinion) and are making decisions about content that can be challenged in court, and would ultimately be challenged with the right amount of suspicion and belief that an offence is taking place.
jgmitchell: Yes and no. To decode the URL from the HTTPS request, the adversary would have to decrypt and reencrypt the stream – which would amount to a man-in-the-middle attack. Which is not only much more resource-intensive, but also is immediately visible as the server’s certificate signature (or, in case of selfsigned certs, the fingerprint) is changed. Also, such wiretapping on encrypted communications may be legally risky. Your proposed solutions would of course work as well.
Ian D. Nock,
(First, feel free to leave that comment on my actual blog; what you see above is an auto-generated trackback thingy).
Second, what’s the difference between stick figures described as minors doing it and the sticks that make up the words creating the description you suggest would criminalize my depiction? In other words, words are stick figures, and once you start censoring the content of words (stick figure or no), you open the door to having any words censored for any reason. For, who is to judge?
Censorship is a double-edged sword.
The words give the drawing context, this is what can give criminality to something that is otherwise grey.
@ThinkConstructive
Crossed wires, until I followed up on Cleanfeed in the last hour I assumed that only the 6 ISPs specifically mentioned in the Wikipedia/Zappa album cover controversy use Cleanfeed. I’m not a customer of any of these ISPs but I guess I do have to assume that I’m one of the 95% of UK broadband users whose ISP has implemented Cleanfeed. So, my point about individual choice is somewhat moot, but at least OpenDNS does give allow me choice to coarsely filter, by domain, sites I wish to deny my family access to.
That Cleanfeed is a less than precise solution and catches URLs entirely unrelated to the IWF’s mission is a pain in the arse. However, I can accept Cleanfeed’s overspill if it’s satisfying its goal, if the ISPs (like PlusNet) are willing to resolve errors and if the IWF provides a corrective procedure for mis-rated content . The latter needs to be effective and efficient.
My privacy point is perhaps a little conspiratorial but the Home Office Transposition of Directive 2006/24/EC proposals to track all UK online activity piqued my curiosity as to how logging could possibly be implemented without massive data collection but this explanation of the Cleanfeed architecture alludes to a focussed logging solution: direct the data collection against suspicious target URLs, log the source & target addresses, retain data for 18 months, etc. If such a solution was implemented then my inocuous meanderings through the web-o-sphere could remain private but if I were to cross to the wild side I’d be leaving a trail. That’s just about as acceptable as a speed camera on the public highway.
Alternately, I’ll sucumb to my paranoia and create my own AMI as a VPN exit node on EC2 and wait for the knock on the door to ask why?
[…] Great Firewall of Britain […]
Interesting. I wonder what they are doing to protect people from phishing sites? Are they putting in the same effort?
Or is that politically incorrect?
Having myself been hit with several viruses, one of witch tapped into a bank account, (we did get the money back) I’d like to know what they are doing in that respect?
I’ll have to look up what their guidelines are concerning “Child Porn.” Is there an international guideline or treaty?
Seems that with a lot of governments the attacks on Sept 11, 2001 was a godsend. They can use that to hide behind while trying to control as much as they want too.
Of course, had the American Government employees and elected officials actually been doing the jobs they are paid to do, the attacks would never have happened in the first place.
My take on such things as blocking sites that governments have deemed, shall we say, a, “threat?” is this: Just stop using the net. Or reduce your use to the minimum.
Okay, you say, “Why?”
Simple. The massive drop in traffic, the service providers will scream bloody murder.
The drop in advertising sales, use, taxes, and what have you will have a profound effect. I mean, we lived without the internet until the early 1990’s. And did so for thousands of years.
But we’d show the governments that the people, not the politicians and government employees own and run the country. Not them.
@MJ Ray – The kit is not operated by a “self-regulating” third party, it’s operated by us. Like I said, it’s our kit, our engineers built the platform, and our engineers maintain the platform. We don’t call it cleanfeed either, that’s what BT Retail called their implementation AFAIK.
@Anonymouse, the IWF do not have administrative access to our proxies. There’s an old post from last year on our forums that you may find of interest here – http://community.plus.net/forum/index.php/topic,58568.msg479927.html#msg479927
[…] if you want to know more about how this works technically there is a very good write up on The Nock Blog about how PlusNet work this, I personally am with Orange and I can’t access the Wikipedia […]
@Bob Pullen, informative – thanks!
Plusnet and Virgin have formally commented, as found on ISP Review
http://www.ispreview.co.uk/news/EkkllEZZFVzYGsGAWz.html
“There is a load of noise being generated right now about Wikipedia being filtered by six of Britain’s largest ISPs because of instances of child pornography being found on certain articles.”
Instances of child pornography? On the contrary, it was only a single instance of a nude girl, which has never been ruled to be child pornography by any legal authority.
Child Pornagraphy, maybe not – that would be for a court to decide.
Offensive, bad taste, nasty.. yes.
[…] The IWF has now backed down from censoring an image on Wikipedia, the censorship of which was adjudged by many to be too wide ranging by taking in the entire page, in addition to the fact that the image (although not nice) was generally available in libraries, record stores and online download services. The secondary impact was the blocking of anonymous editing of Wikipedia from the whole of the UK due to mechanism of filtering used, as presented on my personal blog. […]
[…] sites containing illegal child pornography. Because of some technicalities that are well explained here, that led to Wikipedia being uneditable from most computers in the UK. There was a furor, the […]
[…] That caused large swaths of Wikipedia to be inaccessible across the pond; the IWF’s blacklist also blocked access to parts of Flickr and, yes, Ning (though apparently not the dirty […]
Somewhat more detailed diagrams are published here:
It’s a sales presentation of the censorship system.
The presentation can be downloaded as a PDF file.
[…] it, so that’s the purpose of this blog. The Plusnet IWF implementation has been covered on The Nock Blog, BoingBoing the The Guardian. The Wikipedia coverage can be read on […]
[…] found a link to an excellent description of how the platform works, think basic – very basic. I know that whatever solution is used needs to be low touch because of […]
[…] Great Firewall of Britain « The Nock Blog (tags: security privacy news technology surveillance uk wikipedia proxy ning) […]
[…] Great Firewall of Britain […]
There’s a lot of useful information on this site.
Thanks a lot!
but! because it is interpreted as a “proxy” and rerouted from there, all requests for perfectly innocuous downloads are seen by the end site as coming from one address, and denied on “excess traffic” grounds.
this strangles perfectly legitimate web traffic, and is no different to blanket blocking. it is also unacceptably surreptitious
It only applies the transparent proxy to sites on a specific blacklist. Most sites go straight through.
[…] to Nocky. As Boing Boing comments, Translation: a third party now monitors every request made to Wikipedia […]
There’s a lot of useful information on this site.
Thanks a lot!
[…] and for some reason also included sites such as dental practices etc. Here is an old post about it https://nocky100.wordpress.com/2008/1…ll-of-britain/ __________________ Manage your portfolio using my new Domain Portfolio Management script. […]
[…] Great Firewall of Britain « The Nock Blog Share this:EmailRedditDiggStumbleUpon ← “Apart from anything else, as we have seen from the iPlayer, and the development of services in the US such as YouTube and Hulu (a joint venture between NBC Universal and News Corp), the media market… “She betrays the classic symptoms of a contemporary malaise that teachers talk about all the time: noisy assertiveness masking a desperate lack of genuine self-esteem.” → […]